How Does An Exploit Kit Work? What Is It?
Attackers employ automated programs called exploit kits (also known as exploit packs) to take advantage of well-known flaws in systems or applications. They can be used to covertly initiate attacks while targets are online with the intention of downloading and executing malware.
We go into further detail about what is an exploit kit, how does an exploit kit work, and how cybercriminals utilize them in this post. We’ll also offer advice on avoiding attacks and the malware payload they produce.
Table of Contents
What Is An Exploit Kit?
exploit kits are automatic threats that use compromised websites to divert network traffic, scan browser-based vulnerable applications, and run malware
exploit kits are developed to automatically and silently exploit vulnerabilities on a victim’s machine while browsing the web. Due to their highly automated nature, exploiting toolkits has become one of the most popular methods for mass malware or remote access tools (rats) distribution by criminal groups, lowering the barriers to entry for attackers. exploit kits can also be effective at generating profits for malicious actors. exploit kit creators offer these rentals in the form of exploit kits as a service on the criminal underground market, where prices for major kits can run into thousands of dollars per month.
The ultimate goal of an attacker with an attack toolkit is to establish control over the device in an automated and simplified manner. In an exploit kit, a series of events must occur for the infection to succeed. Each stage, starting with the login page, through the execution of the exploit attack, and through the delivery of the payload, must be successfully completed in order for the attacker to gain control of the host.
How Does An Exploit Kit Work?
exploit attacks are often the first part of a larger attack. Hackers scan outdated systems for critical vulnerabilities and then exploit them by deploying targeted malware. exploit attacks typically include shell code, which is a small malware payload used to download other malware from a network controlled by the attacker. The shell code allows hackers to infect devices and infiltrate organizations.
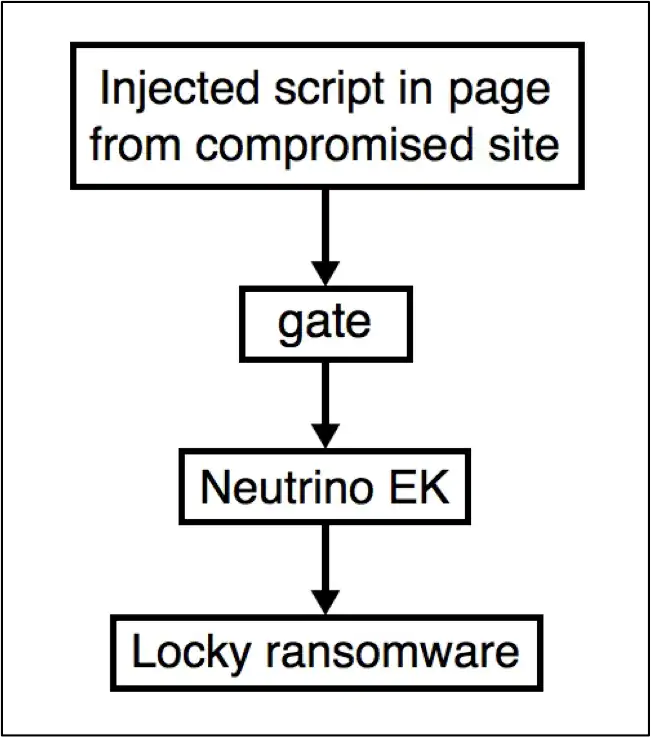
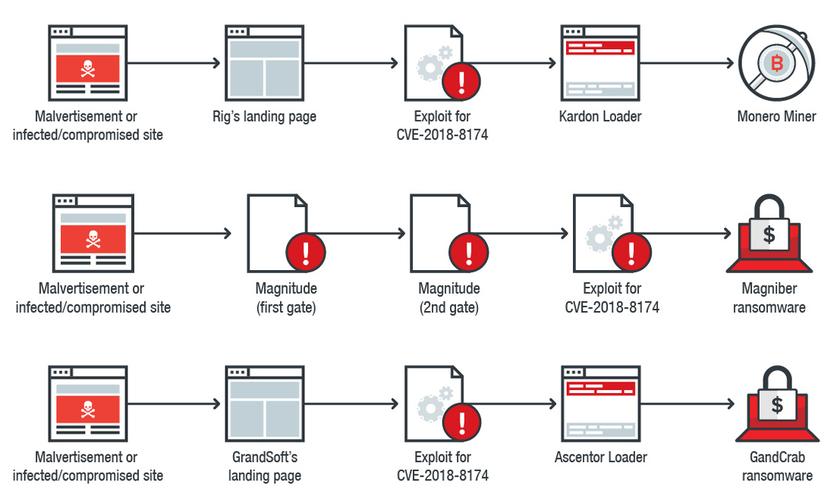
An exploit kit is a more comprehensive tool that contains a set of vulnerabilities. These toolkits scan the device for different types of software vulnerabilities, and if they detect any, they deploy additional malware to further infect the device. The toolkit can use vulnerabilities against a variety of software, including Adobe Flash Player, Adobe Reader, Internet Explorer, Oracle Java, and Sun Java.
The most common way for attackers to distribute exploits and exploit kits is through web pages, but exploits can also arrive via email. Some websites unknowingly and unwillingly place malicious code and vulnerabilities in their ads.
The infographic below shows how an exploit kit might try to exploit the device after you visit the compromised web page.
How To Implement An Exploit Kit?
There are several stages to successfully exploit an exploit:
The login page establishes contact with the host environment.
Redirect to another login page to detect vulnerabilities in the host that could be exploited.
Use this exploit to spread malware.
Infects the host environment by executing malware.
The exploit kit contains all the code needed to execute each stage. If a phase is unsuccessful, the attack on that particular device is over. Here, we’ll look at these phases in more detail and examine what criteria each phase needs to meet.
Make Connections
The first stage of exploiting the exploit uses the login page of the site that has been compromised. Victims are encouraged to visit this site, for example through email links, pop-ups, or malicious ads (malicious ads).
Once the victim clicks on a link to the site or enters a URL into their browser, initial contact is made.
At this point, there may be some users who do not meet certain criteria, such as users in the wrong location (usually determined by IP address or installation language checking). These users are filtered out, and for them, the attack is over.
Redirect
The remaining victims were redirected to another login page, which was no longer a real website. The code embedded in this landing page then proceeds to determine if the victim’s device has any browser-based vulnerable applications that correspond to the exploit attack in the suite.
If no exploit is detected (that is, all vulnerabilities are up to date and all vulnerabilities have been patched), the attack stops. But if an exploit is found, the website will send traffic to that exploit.
Use
The exploit is needed because the attack kit requires the malware to run on the host environment (the victim’s device). The apps found to be vulnerable were used to download malware.
How Exploit executes depends on the application. For example, if the web browser itself is the target, the exploit will take the form of code embedded in the web page. Another example is an application that typically targets Microsoft Silverlight, where the exploit is a file.
Microsoft Silverlight home page.
The term “exploit kit” means having multiple vulnerabilities bundled into a single package. It will target multiple vulnerabilities, making it easy to enforce and increasing the chances of success for criminals.
Infection
After successful exploitation, the malware is executed in the victim’s environment. There are many different scenarios in terms of the impact of malware. exploit attack kits can be used to spread various types of malware, including ransomware and Trojan horses, such as the Remote Access Trojan Horse.
A common use for exploit kits is to execute cryptocurrency mining software. This hijacks the victim’s computer resources for mining bitcoin and other cryptocurrencies without the user’s permission.
How To Prevent Attack Exploit Kits?
Because it’s hard to know when exploit kits work and how diverse they are, it’s best to avoid them in the first place. Here are some helpful tips:
Keep software up to date. One of the most important reasons for regular software updates is to patch security holes.
Don’t click on spam links. As always, you should avoid opening emails from anyone you don’t know, and definitely don’t click on suspicious links.
Avoid ads and pop-ups. When it comes to pop-ups and ads, it’s hard to avoid clicking, as many pop-ups and ads are designed to trick you into doing so (for example, the “Close” button is hard to locate or ads move around). AD blockers can help because they prevent ads and pop-ups from appearing in the first place.
Use antivirus software. Antivirus software is not foolproof by any means, but it can detect and remove many known threats, including viruses and other types of malware that get into your device.
Conclusion
Because exploit kits operate in the background, it may be challenging to detect attacks. However, you can take precautions to defend yourself from these assaults, such as avoiding unfamiliar links and maintaining software updates.

